Refer to the exhibit. You have a non-Cisco switch that is not communicating properly while connected to the distribution-layer Cisco switching fabric.Which two best-practice actions can you take to overcome this problem? ()(Choose two.)A. Turn off MST (802.1s) on all switches.B. Turn on MST (802.1s) on all switches.C. Turn on RSTP (802.1w) on all switches.D. Turn off RSTP (802.1w) on all switches.
Refer to the exhibit. You have a non-Cisco switch that is not communicating properly while connected to the distribution-layer Cisco switching fabric.Which two best-practice actions can you take to overcome this problem? ()(Choose two.)
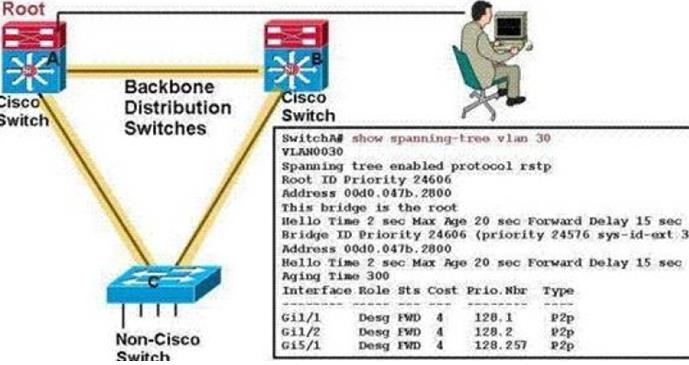
A. Turn off MST (802.1s) on all switches.
B. Turn on MST (802.1s) on all switches.
C. Turn on RSTP (802.1w) on all switches.
D. Turn off RSTP (802.1w) on all switches.
相关考题:
在防范食品污染方面,你们采取什么措施?A.What measures will you take against food pollution?B.What actions will you take for selecting food?C.How will you prevent the food from being polluted?D.Have you taken any measures against food pollution?
Some of you may have finished unitone, _______, you can move onto unit two. A、if you mayB、if you doC、if notD、if so
Having acknowledged receipt of the interview letter,you must prepare for the interview. Firms usually take a good deal of trouble over interviews,and there may be three or more people present,which can be a little frightening. Very often the personnel officer will begin by some words of welcome and an invitation to you to tell them a little about yourself. This is really inviting you to repeat the information you have already supplied on the application form,and which they have already read,but it does have some point. It will put you at your ease,because at least you know all about your own level of achievement and can speak about it confidently. It helps them assess your ability to communicate and your serf-esteem. Some people have too high an opinion of themselves,some take an unduly pessimistic view of their achievements,while others have a nicely balanced assessment of their own abilities.
Some of you may have finished unit one. _____ , you can go on to unit two.A. If you mayB. If you doC. If notD. If so
听力原文:Your check is a forward one. We will make payment at the maturity.(3)A.You can have the check encashed now.B.You will have the money in one or two days.C.You can not have the check encashed.D.You have to wait for the payment till the maturity.
You are the administrator of a Windows 2000 network. The network includes a Windows 2000 Server computer that is used as a file server. More than 800 of Ezonexam.com's client computers are connected to this server.A shared folder named Data on the server is on an NTFS partition. The data folder contains more than 200 files. The permissions for the data folder are shown in the following table.Type of permission Account PermissionShare Users ChangeNTFS Users Full ControlYou discover that users are connected to the Data folder. You have an immediate need to prevent 10 of the files in the Data folder from being modified. You want your actions to have the smallest possible effects on the users who are using other files on the server.What two actions should you take? (Choose Two)A.Modify the NTFS permissions for the 10 files.B.Modify the NTFS permissions for the Data folder.C.Modify the shared permissions for the Data folder.D.Log off the users from the network.E.Disconnect the users from the Data folder.
You have a computer that runs Windows Vista. You create a virtual private network (VPN) connection between the computer and your company’s network.You notice that while the computer is connected through the VPN connection, users on the company network can access shared folders on the computer.You need to prevent network users from accessing your shared folders when you are connected to the company’s network by using the VPN connection.What should you do?()A.AB.BC.CD.D
You have a computer that runs Windows Vista.You connect to your company’s network by using a virtual private network (VPN) connection. You notice that when you establish the VPN connection, you are unable to access Internet Web sites. When you disconnect the VPN connection, you can access Internet Web sites.You need to access Internet Web sites while you are connected to the VPN connection.What should you do?()A.AB.BC.CD.D
While troubleshooting a network outage, you discover that an employee brought a switch from home into the office to connect additional equipment to the network. In order to increase his speed, he connected this switch to both network ports in his office, resulting in a bridge loop.Which of these can you implement to prevent future occurrences of this issue?()A.RSTPB.root guardC.BPDU guardD.GLBP
Refer to the exhibit. You want to use all the routes in the EIGRP topology for IP load balancing. Which two EIGRP subcommands wou ld you use to accomplish this goal?() A. traffic - share balancedB. distanceC. maximum- pathsD. default - networkE. variance
Refer to the exhibit. You have completed an OSPF implementation, and you are verifying OSPF operation. You notice that router A and router B are stuck in the two - way state. From the show ip ospf interface command output, what is the cause of this issue?()A. All OSPF implementations must have at le ast one interface in area 0.B. You are attempting to run in the broadcast mode over an NBMA interface.C. Both routers are configured to function as a BDR; therefore, there is no DR router.D. Someone has changed the OSPF router ID; therefore you must clear the OSPF process.E. The OSPF priority is set to 0 on both routers; therefore neither can become the DR.
Refer to the exhibit. You are the network administrator of the Route.com company. You have been tasked to implement a hub and spoke EIGRP topology over Frame Relay to provide connectivity between the networks at headquarters and all 300 spokes. Before you begin the actual implementation, which three pieces of information are more important to know than the others?()A. the Committed Information Rate of all the Frame Relay PVCsB. the Cisco IOS version running on all the routersC. the router model number of all the spoke routersD. the number of HQ networks connected behind the headquarter routersE. the routing policy, such as whether or not the spokes can be used as backup transient point between the two headquarter routers
To which switch or switches should you provide redundant links in order to achieve high availability with reliable fast convergence in the enterprise campus?() A. to a core switch running Cisco NSF and SSO from redundant distribution switches connected with a Layer 2 linkB. to a core switch running Cisco NSF and SSO from redundant distribution switches connected with a Layer 3 linkC. to two core switches from redundant distribution switches connected with a Layer 2 linkD. to two core switches from redundant distribution switches connected with a Layer 3 linkE. to two core switches running Cisco NSF and SSO from two redundant distribution switches running Cisco NSF and SSO
Refer to the exhibit. Given the output shown from this Cisco Catalyst 2950, what is the most likely reason that interface FastEthernet 0/10 is not the root port for VLAN 2?() A.This switch has more than one interface connected to the root network segment in VLAN 2.B.This switch is running RSTP while the elected designated switch is running 802.1d Spanning Tree.C.This switch interface has a higher path cost to the root bridge than another in the topology.D.This switch has a lower bridge ID for VLAN 2 than the elected designated switch.
Questions 85-87 refer to the following advertisement.Gaining green card may involve the black market costs. The green card application process can take a long time, and people often have to eat while waiting for their papers. Many immigrants have resolved this through the acquisition of fake documents. (Note as an attorney, I emphatically do not recommend this. But people do it. A lot.) At their best (and most expensive), fake papers can be quite useful. From talking to immigrants, I have learned that there is a man in a certain Central American capital who, for $6000, will get you a U.S. passport with a name and photo of your choosing that will scan as real on border crossing computers. In New York City, $150-$200 will get you work documents connected to a real Social Security number. $75 will get you a color copy on thick paper that looks like a Social Security card as long as you don’t look closely enough to see that it is actually a “Social Security” card.What does the underlined word “this” refer to?A. The problem of long-time waiting for papersB. The lack of food during the application processC. The costs of fake documents in black marketD. The illegal nature of the black market business
To which switch or switches should you provide redundant links in order to achieve high availability with reliable fast convergence in the enterprise campus?()A、 to a core switch running Cisco NSF and SSO from redundant distribution switches connected with a Layer 2 linkB、 to a core switch running Cisco NSF and SSO from redundant distribution switches connected with a Layer 3 linkC、 to two core switches from redundant distribution switches connected with Layer 2 linkD、 to two core switches from redundant distribution switches connected with Layer 3 linkE、 to two core switches running Cisco NSF and SSO from two redundant distribution switches running Cisco NSF and SSO
Which two statements about configuration an unconnected Catalyst Express 500 switch from setup mode using a PC are true?()A、You may use Cisco Network Assistant to set up the initial configurationB、You must use CLI for initial configurationC、You may use either CLI or CAN for configurationD、You may make a direct connection to the PC from any point on the switchE、You may only make a direct connection from the port with the flashing green LED to the PC
You are charged with implementing a secure wireless installation which will provide Internet accessto client devices but will not allow communications between wireless clients. In addition to implementing PSPF or peer-to-peer blocking on the wireless side. Which of the following actions should you perform on the wired infrastructure?()A、Implement a Cisco Secure IPS sensor.B、Implement 802.1X on the switch ports.C、Take no action, you have achieved your goal.D、Implement a protected port on the access switches.
A new switch is being installed and you have been assigned the task of connecting it to an existing switch. In doing this, you want to set up the VLAN Trunking Protocol so that VLAN information can be passed between the switches. Which of the following must you do to accomplish this?()A、You must set each end of the trunk line to IEEE 802.1e encapsulation.B、You must set the same VTP management domain name on both switches.C、You must set all ports on the two switches as access ports.D、You must configure one of the switches as a VTP server.E、You must use a rollover cable to connect the two switches.
You work as an administrator at ABC.com. The ABC.com network consists of a single domain named ABC.com. All servers in the ABC.com domain, including domain controllers, have Windows Server 2012 R2 installed.ABC.com has a server, named ABC-SR07, which has four network adapters. ABC.com has two local area networks (LANs). Two of ABC-SR07’s network adapters are connected to the one LAN,while the other two are connected to the other LAN.You are required to configure one of the network adapter pairs into a network adapter team. Which of the following actions should you take?()A、You should consider accessing the Group Policy Management Console (GPMC) on ABC-SR07.B、You should consider accessing the TS Manager console on ABC-SR07.C、You should consider accessing the Server Manager console on ABC-SR07.D、You should consider accessing the Remote Desktop Gateway Manager console on ABC-SR07.
多选题While Monitoring the space usage in your database that is in ARCHIVELOG mode you observed that the flash recovery area does not have enough free space to accommodate any more files and you do not have necessary permissions to add more space to it. Identify the two events that can occur in the event of a log switch? ()(Choose two.)AAn entry is created in the alert log file and the database instance continues to function normallyBThe log switch hangs occur for transactions until free space is available in the flash recovery areaCThe Oracle database server deletes a file that is on the obsolete file list to make free space in the flash recovery areaDThe database instance status is implicitly changed to RESTRICTED mode and file creations to the flash recovery area are prevented
单选题While troubleshooting a network outage, you discover that an employee brought a switch from home into the office to connect additional equipment to the network. In order to increase his speed, he connected this switch to both network ports in his office, resulting in a bridge loop. Which of these can you implement to prevent future occurrences of this issue?()ARSTPBroot guardCBPDU guardDGLBP
单选题To which switch or switches should you provide redundant links in order to achieve high availability with reliable fast convergence in the enterprise campus?()A to a core switch running Cisco NSF and SSO from redundant distribution switches connected with a Layer 2 linkB to a core switch running Cisco NSF and SSO from redundant distribution switches connected with a Layer 3 linkC to two core switches from redundant distribution switches connected with Layer 2 linkD to two core switches from redundant distribution switches connected with Layer 3 linkE to two core switches running Cisco NSF and SSO from two redundant distribution switches running Cisco NSF and SSO
多选题You have just purchased a new Cisco 3560 switch running the enhanced IOS and need configure it to be installed in a high availability network. On a 3560 EMI switch, which three types of interfaces can be used to configure HSRP?()ASVI interfaceBAccess portCEtherChannel port channelDLoopback interfaceERouted portFBVI interface
单选题Careth: Good afternoon. I’ve just joined the library. How many books can I take out? Eunice: You can take two books, and keep them for ten days. If you haven’t finished, you can renew them. Careth: How do I do that? ________ Eunice: No, you can telephone. Tell us the titles of the books, and the date they are due for return. Eunice: These two books have been lended.AWhy can’t I keep them for a longer time?BMust I visit the library?CHow much could I be fined?DCan I lend them to my friends?
单选题Must I take a taxi? No, you(). You can take my car.Ahad better toBdon'tCmust notDdon't have to