You are an experienced network administrator in an international company. During your working hours, customers complain that they experience intermittent data loss and they intermittently fail to connect to crucial servers. As shown in the following topology, the 802.1Q trunk between DSW111 and ASW1 fails. Though DSW112 is in the service of HSRP group 11, the SVI for VLAN 11 is up on DSW111.So as to figure out the problem,which three commands should you issue on DSW111? ()(Choose three.)A. show standby vlan 11 briefB. show interfaces vlan 11C. show spanning-tree vlan 11D. show interfacesmod/port trunk
You are an experienced network administrator in an international company. During your working hours, customers complain that they experience intermittent data loss and they intermittently fail to connect to crucial servers. As shown in the following topology, the 802.1Q trunk between DSW111 and ASW1 fails. Though DSW112 is in the service of HSRP group 11, the SVI for VLAN 11 is up on DSW111.So as to figure out the problem,which three commands should you issue on DSW111? ()(Choose three.)
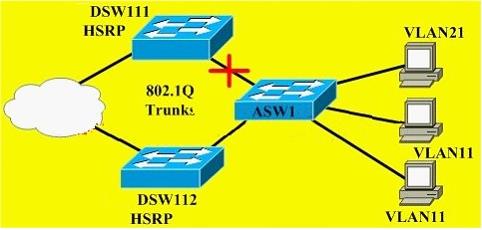
A. show standby vlan 11 brief
B. show interfaces vlan 11
C. show spanning-tree vlan 11
D. show interfaces
相关考题:
You are a network administrator for your company. You currently automate backups of the System State data on the servers in your network by using NTBackup. Your manager instructs you to document the procedure for restoring a server from a backup of the System State data.You need to select the correct method for performing a restoration of a backup of the System State data.What should you do?()A. Run the following command: ntbackup.exe backup /F {FileName}B. Run the following command: ntbackup.exe backup systemstate /F {FileName}C. In Control Panel, open System, and configure the Startup and Recovery settings on the Advanced tab.D. Use NTBackup interactively.
According to your resume, you have had some experience working in a foreign company. May I ask you why you left?
You are an experienced network administrator in an international corporation. During your working hours, you are asked to deploy the Cisco SSL VPN AIM module in a Cisco 1800 Series Router. The beneficial reason for that deployment is to:()A. improve performance up to 300% for both IPsec and SSL VPN applicationsB. improve performance for both IPsec and SSL VPN applications with IPsec encryption taking place in hardwareC. improve performance up to 300% for both IPsec and SSL VPN applications with SSL encryption taking place in hardwareD. improve performance up to 200% for both IPsec and SSL VPN applications with encryption taking place in hardwareE. improve performance exclusively for SSL VPN applications
You are an experienced network administrator in an international corporation. One of your clients asks you to configure a network for a financial trading center which requires multiple high-value transactions.And the transactions are very important to the client. In such a situation, which two of the following are basic and most important requirements concerning the configuration? ()(Choose two.)A. no single point of failureB. determine which protocol to useC. trading database server locationD. deterministic response to all failures
You work as a network administrator in your company. Communication inside the company is ensured by network environments, such as GET VPN, Dynamic Multipoint VPN and Ethernet.Which PIN architecture is applicable in those environments?()A.CampusB.TeleworkerC.BranchD.Data center
You are an experienced network administrator in an international corporation. During your working hours, you are asked to deploy the Cisco SSL VPN AIM module in a Cisco 1800 Series Router. The beneficial reason for that deployment is to:()A、improve performance up to 300% for both IPsec and SSL VPN applicationsB、improve performance for both IPsec and SSL VPN applications with IPsec encryption taking place in hardwareC、improve performance up to 300% for both IPsec and SSL VPN applications with SSL encryption taking place in hardwareD、improve performance up to 200% for both IPsec and SSL VPN applications with encryption taking place in hardwareE、improve performance exclusively for SSL VPN applications
You are an experienced network administrator in an international corporation. One of your clients asks you to configure a network for a financial trading center which requires multiple high-value transactions. And the transactions are very important to the client. In such a situation, which two of the following are basic and most important requirements concerning the configuration? ()(Choose two.)A、no single point of failureB、determine which protocol to useC、trading database server locationD、deterministic response to all failures
You work as a network administrator in your company. Communication inside the company is ensured by network environments, such as GET VPN, Dynamic Multipoint VPN and Ethernet. Which PIN architecture is applicable in those environments?()A、CampusB、TeleworkerC、BranchD、Data center
You are a network administrator for your company. The company has a main office and two branch offices. The branch offices are connected to the main office by T1 lines. The network consists of three Active Directory sites, one for each office. All client computers run either Windows 2000 Professional or Windows XP Professional. Each office has a small data center that contains domain controllers, WINS, DNS, and DHCP servers, all running Windows Server 2003. Users in all offices connect to a file server in the main office to retrieve critical files. The network team reports that the WAN connections are severely congested during peak business hours. Users report poor file server performance during peak business hours. The design team is concerned that the file server is a single point of failure. The design team requests a plan to alleviate the WAN congestion during business hours and to provide high availability for the file server. You need to provide a solution that improves file server performance during peak hours and that provides high availability for file services. You need to minimize bandwidth utilization. What should you do? ()A、 Purchase two high-end servers and a shared fiber-attached disk array. Implement a file server cluster in the main office by using both new servers and the shared fiber-attached disk array.B、 Implement Offline Files on the client computers in the branch offices by using Synchronization Manager. Schedule synchronization to occur during off-peak hours.C、 Implement a stand-alone Distributed File System (DFS) root in the main office. Implement copies of shared folders for the branch offices. Schedule replication of shared folders to occur during off-peak hours by using scheduled tasks.D、 Implement a domain Distributed File System (DFS) root in the main office. Implement DFS replicas for the branch offices. Schedule replication to occur during off-peak hours.
You are a database administrator for your company. The company uses a SQL Server 2005 application. Each night, data is imported into a database, and the database is then set to be read-only. During business hours, users run predefined and ad hoc queries. You need to monitor the servers performance during the day. What are two possible ways to achieve this goal?()A、Use the Lock Waits/sec performance counter.B、Use the Number of Deadlocks/sec performance counter.C、Use the Transactions/sec performance counter.D、Use the Full Scans/sec performance counter.E、Use the Batches/sec performance counter.
You are a network administrator for your company. The network contains a perimeter network. The perimeter network contains four Windows Server 2003, Web Edition computers that are configured as a Network Load Balancing cluster. The cluster hosts an e-commerce Web site that must be available 24 hours per day. The cluster is located in a physically secure data center and uses an Internet-addressable virtual IP address. All servers in the cluster are configured with the Hisecws.inf template. You need to implement protective measures against the cluster’s most significant security vulnerability. What should you do? ()A、 Use Encrypting File System (EFS) for all files that contain confidential data stored on the cluster.B、 Use packet filtering on all inbound traffic to the cluster.C、 Use Security Configuration and Analysis regularly to compare the security settings on all servers in the cluster with the baseline settings.D、 Use intrusion detection on the perimeter network.
You are a professional level SQL Server 2005 database administrator in an international corporation named Wiikigo. You are experienced in implementing high-availability solutions, monitoring the database server, and design deployment. In the company, you major job is the deployment, maintenance and support of Microsoft SQL Server 2005. You work as a database administrator for your company. A user database named Products is included by your SQL Server 2005 computer. SQL Server Integration Services (SSIS) packages are utilized to export data from the Products database to a text file. You deliver the text file to your company’s trading partners by utilizing FTP. You are required to make sure that your SSIS packages can be recovered from the occurrence of a disaster. Which action should be performed to finish the task?()A、To finish the task,the Products database should be backed up.B、To finish the task,your server should be set to utilize the full recovery model.C、To finish the task,your server should be set to utilize the bulk-logged recovery model.D、To finish the task, the msdb database should be backed up.
You are a professional level SQL Server 2005 database administrator in an international corporation named Wiikigo. You are experienced in implementing high-availability solutions, monitoring the database server, and design deployment. In the company, you major job is the deployment, maintenance and support of Microsoft SQL Server 2005. You work as a database administrator for your company. A SQL Server 2005 application is utilized by the company. A query is executed by the application to return three columns of the nvarchar data type and one column of the XML data type. A WHERE clause is utilized by the query, and all three of the nvarchar columns are contained by the WHERE clause. 5 million rows are included by the table, and 50,000 rows are returned by the query. The performance of the query should be enhanced. Which action should be performed to achieve the goal?()A、A primary XML index should be created on the XML column.B、Statistics should be created on the nvarchar columns.C、A view should be created, and only the four columns that the query utilizes are contained by a view.D、A composite index should be created on the three nvarchar columns, and INCLUDE should be specified for the XML column.
You work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a database named DB1 in the instance. At present about 90 GB of data is stored in DB1. You made some rough calculations that every day about 1 GB of data is modified or inserted. You set the recovery model of DB1 to Simple. According to the company requirements, during business hours, data loss of more than 120 minutes worth of transactions is unacceptable. You have to choose a backup strategy which must comply with the following two requirements: Using as little disk space as possible Complying with the company requirements. So what action should you perform to achieve this goal?() A、A full database backup should be performed once daily. During business hour, a transaction log backup should be performed every two hours. B、A full database backup should be performed once daily C、A full database backup should be performed once daily. During business hours, a differential backup should be performed every two hours D、Perform a full database backup should be performed once every week. A differential backup should be performed once daily. During business hours a transaction log backup should be performed every two hours.
You are the network administrator for your company. The network consists of a single Active Directory domain. The network contains an application server running Windows Server 2003. Users report intermittent slow performance when they access the application server throughout the day. You find out that the network interface on the application server is being heavily used during the periods of slow performance. You suspect that a single computer is causing the problem.You need to create a plan to identify the problem computer. What should you do?()A、 Monitor the performance monitor counters on the application server by using System Monitor. B、 Monitor the network traffic on the application server by using Network Monitor.C、 Monitor network statistics on the application server by using Task Manager.D、 Run network diagnostics on the application server by using Network Diagnostics.
You are a security administrator for your company. The network consists of a single Active Directory domain. All servers run Windows 2003 Server. All client computers run Windows XP Professional. All computers are configured to use Automatic Updates to install updates without user intervention. Updates are scheduled to occur during o peak hours. During a security audit,you notice some client computers are not receiving updates on a regular basis. You verify that Automatic Updates is running on All client computers, and you verify that users cannot modify the Automatic Updates settings. You need to ensure that computers on your network receive all updates. What should you do?()A、 Enable the No auto-restart for scheduled Automatic Updates installations setting.B、 Disable the Specify intranet Microsoft update service location setting.C、 Enable the Remove access to use all Windows Update features setting.D、 Enable the Reschedule Automatic Updates scheduled installations setting.
You are a network administrator for your company. You currently automate backups of the System State data on the servers in your network by using NTBackup. Your manager instructs you to document the procedure for restoring a server from a backup of the System State data.You need to select the correct method for performing a restoration of a backup of the System State data.What should you do?()A、Run the following command: ntbackup.exe backup /F {"FileName"}B、Run the following command: ntbackup.exe backup systemstate /F {"FileName"}C、In Control Panel, open System, and configure the Startup and Recovery settings on the Advanced tab.D、Use NTBackup interactively.
单选题You are the network administrator for your company. The network consists of a single Active Directory domain. All network servers run Windows Server 2003. The domain contains three domain controllers: DC1, DC2, and DC3. Each one hosts user data. DC1 experiences hard disk failure. You need to temporarily restore the user data to DC2. Which type of restoration should you perform? ()AAutomated System Recovery (ASR)BnormalCprimaryDauthoritative
单选题You are the network administrator for . Your network consists of a single Active Directory domain named All network servers runWindows Server 2003. You use Microsoft Operations Manager (MOM) to monitor all servers. An e-mail server named MailTK1 is located at a remote data center. MailTK1 runs Microsoft Exchange Server 2003. MailTK1 restarts unexpectedly during business hours. The event log indicates a problem with the SCSI CD-ROM. You need to ensure that MailTK1 remains continuously available during business hours. What should you do?()AUse Device Manager to disable the SCSI CD-ROM.BCreate and implement a new hardware profile to exclude the SCSI CD-ROM.CUse Device Manager to update the driver for the SCSI CD-ROM.DUse Device Manager to update the driver for the SCSI controller.
单选题You are the network administrator for your company. All network servers run Windows Server 2003. Business hours are 8 A.M. to 5 P.M. You provide network assistance during business hours only. A server named Server1 stores personal files for all network users. Mobile users access Server1 by using the company's VPN. They must have 24-hour access to the files on Server1. You need to be able to identify the source of the recurring slowdowns in VPN access. First, you log on to Server1. What should you do next?()AUse Task Manager to review network utilization of the VPN adapter.BUse the Performance console to create a log of network utilization outside of business hours.CUse System Monitor to review network utilization of the VPN connection.DUse Task Manager to select Bytes Sent as the Network Adapter History setting.
单选题You are the administrator of your company’s network. Using Windows Installer packages, you want to install customized versions of Microsoft Excel on different departments in the company. Which type of file should you apply to the installation database?()AmsiBmstCzapDzip
单选题You work as a network administrator in your company. Communication inside the company is ensured by network environments, such as GET VPN, Dynamic Multipoint VPN and Ethernet. Which PIN architecture is applicable in those environments?()ACampusBTeleworkerCBranchDData center
单选题All client computers on your company network run Windows 7. The Finance department staff run an application that collects data from 09.30 hours to 15.00 hours everyday. After data collection, the application generates reports that contain data aggregation for the day and the previous week. During report generation, the Finance department staff experience slow performance on their computers. You discover that the usage of the processor on these computers is between 90 and 100 percent. You need to reduce the impact of report generation on the Finance computers. What should you do?()ASet the priority of the application to Low.BSet the priority of the application to Real-time.CConfigure the processor affinity mask to ensure that the application uses all the available processors.DModify the memory settings of the computers to optimize the performance of the background applications.
单选题Your network contains a single Active Directory domain. All servers on the network are members of the domain. You have a server named Server1 that runs Windows Server 2003 Service Pack 2 (SP2). Server1 has two NTFS partitions. You create and share a folder named Data in the root of a partition on Server1. You log on to your computer by using the domain Administrator account and discover that you cannot modify files in the Data share. You need to ensure that the Administrator can modify files in the Data share. The solution must use the minimum amount of permissions. What should you do? ()AModify the NTFS permissions on the Data folder.BModify the share permissions on the Data share.CAdd the domain administrator to the local Administrator’s group on Server1.DMove the Data folder to a new file allocation table (FAT) partition. Share the folder by using the default permissions.
多选题You are a database administrator for your company. The company uses a SQL Server 2005 application. Each night, data is imported into a database, and the database is then set to be read-only. During business hours, users run predefined and ad hoc queries. You need to monitor the servers performance during the day. What are two possible ways to achieve this goal?()AUse the Lock Waits/sec performance counter.BUse the Number of Deadlocks/sec performance counter.CUse the Transactions/sec performance counter.DUse the Full Scans/sec performance counter.EUse the Batches/sec performance counter.
单选题You are the network administrator for your company. The network consists of a single Active Directory domain. All network servers run Windows Server 2003. The domain contains three domain controllers: DC1, DC2, and DC3. Each one hosts user data. DC1 experiences hard disk failure. You need to temporarily restore the user data to DC2. Which type of restoration should you perform? ()AAutomated System Recovery (ASR)BnormalCprimaryDauthoritative